A new Golang-based information stealer called Skuld has compromised Windows systems across Europe, Southeast Asia, and the U.S.
“This new malware strain tries to steal sensitive information from its victims,” Trellix researcher Ernesto Fernández Provecho said in a Tuesday analysis. “To accomplish this task, it searches for data stored in applications such as Discord and web browsers; information from the system and files stored in the victim’s folders.”
Skuld, which shares overlaps with publicly available stealers like Creal Stealer, Luna Grabber, and BlackCap Grabber, is the handiwork of a developer who goes by the online alias Deathined on various social media platforms like GitHub, Twitter, Reddit, and Tumblr.https://googleads.g.doubleclick.net/pagead/ads?client=ca-pub-7983783048239650&output=html&h=90&slotname=2185767680&adk=1884131274&adf=4257282429&pi=t.ma~as.2185767680&w=728&fwrn=4&fwrnh=100&lmt=1686923748&rafmt=12&format=728×90&url=https%3A%2F%2Fthehackernews.com%2F2023%2F06%2Fnew-golang-based-skuld-malware-stealing.html&fwr=0&fwrattr=true&rh=90&rw=728&sfro=1&wgl=1&dt=1686939775228&bpp=2&bdt=560&idt=515&shv=r20230614&mjsv=m202306080101&ptt=9&saldr=aa&abxe=1&cookie=ID%3D5604485fd265ab7d-220e8a6d58df0019%3AT%3D1682023517%3ART%3D1686771601%3AS%3DALNI_MZRZpKGtl2P_PjUncQNpTaITwMVHw&gpic=UID%3D00000bfafde4201f%3AT%3D1682023517%3ART%3D1686771601%3AS%3DALNI_MZ7r6MeYnHbeN-7VL4OzLpQ1EVkYw&prev_fmts=0x0&nras=1&correlator=7097688188432&frm=20&pv=1&ga_vid=940081340.1686939776&ga_sid=1686939776&ga_hid=196156120&ga_fc=0&u_tz=330&u_his=1&u_h=900&u_w=1440&u_ah=817&u_aw=1440&u_cd=24&u_sd=2&adx=178&ady=805&biw=1425&bih=729&scr_x=0&scr_y=0&eid=44759875%2C44759926%2C44759837%2C31071756%2C31075307%2C44772268%2C44788441&oid=2&pvsid=2981293768883235&tmod=2124396429&uas=3&nvt=1&fc=1920&brdim=0%2C28%2C0%2C28%2C1440%2C25%2C1440%2C809%2C1440%2C729&vis=1&rsz=%7C%7CeEbr%7C&abl=CS&pfx=0&fu=128&bc=31&ifi=2&uci=a!2&btvi=1&fsb=1&xpc=DyUyeGc6c6&p=https%3A//thehackernews.com&dtd=646
Also spotted by Trellix is a Telegram group named deathinews, indicating that these online avenues could be used to promote the offering in the future as a service for other threat actors.
The malware, upon execution, checks if it’s running in a virtual environment in an attempt to thwart analysis. It further extracts the list of running processes and compares it against a predefined blocklist. Should any process match with those present in the blocklist, Skuld proceeds to terminate the matched process as opposed to terminating itself.
Besides gathering system metadata, the malware possesses capabilities to harvest cookies and credentials stored in web browsers as well as files present in the Windows user profile folders, including Desktop, Documents, Downloads, Pictures, Music, Videos, and OneDrive.
Artifacts analyzed by Trellix show that it’s engineered to corrupt legitimate files associated with Better Discord and Discord Token Protector and inject JavaScript code into the Discord app to siphon backup codes, mirroring a technique similar to that of another Rust-based infostealer recently documented by Trend Micro.
UPCOMING WEBINAR
🔐 Mastering API Security: Understanding Your True Attack Surface
Discover the untapped vulnerabilities in your API ecosystem and take proactive steps towards ironclad security. Join our insightful webinar!Learn, Connect, Grow
Select samples of Skuld also incorporate a clipper module to alter clipboard content and steal cryptocurrency assets by swapping the wallet addresses, which the cybersecurity company theorized is likely in development.
Data exfiltration is achieved by means of an actor-controlled Discord webhook or the Gofile upload service. In the case of the latter, a reference URL to steal the uploaded ZIP file containing the stolen data is sent to the attacker using the same Discord webhook functionality.
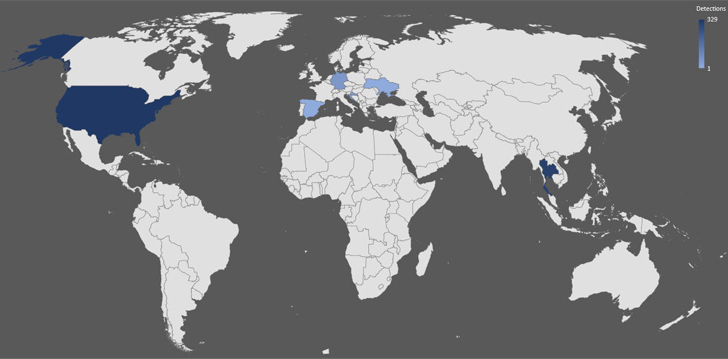
The development points to steady adoption of the Go programming language among threat actors due to its “simplicity, efficiency, and cross-platform compatibility,” thereby making it an attractive vehicle to target multiple operating systems and expand their victim pool.
“Additionally, Golang’s compiled nature lets malware authors produce binary executables that are more challenging to analyze and reverse engineer,” Fernández Provecho noted. “This makes it harder for security researchers and traditional anti-malware solutions to detect and mitigate these threats effectively.”